Dig is an acronym for Domain Information Groper that helps in querying DNS Information and as well as troubleshooting the issue related to it. The dig command is the popular command-line network administrative tool that provides information about the name server as well as host address and various DNS records that we query using the command. It is more flexible and a handful that replaces older tools such as nslookup.
To demonstrate the examples I have used Ubuntu 20.04. This article will help you to look up the various DNS records like A, AAAA, MX, NS, PTR, TXT, DKIM, and SPF. Let’s begin with the installation.
Installation
The dig tool supports various Linux distributions. Following are the commands to install the dig on some popular Linux systems.
Install in Ubuntu/Debian
$ sudo apt install dnsutils
Install in Centos/Fedora
$ sudo yum install bind-utils
Verifying installation by version checking
$ dig –v

Querying Domain ‘A’ Record
By default, the dig command will provide the DNS ‘A’ Record information, and the following is the output after querying the domain.
$ dig google.com
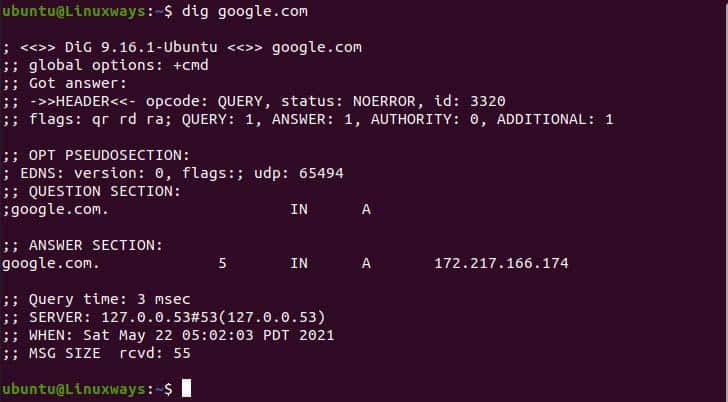
Output after querying the domain.
In the above output, the dig command provides the output in four sections. In the first section, the first row shows the dig version and domain name we look up to. The second row shows the option that is used to query the domain which is (+cmd) by default in the current context. Lastly the headers, it is the response that the server provided during queries. In the flags section in header, qr, rd, and ra refer to query, recursion desired, and recursion available respectively which determine answer format.
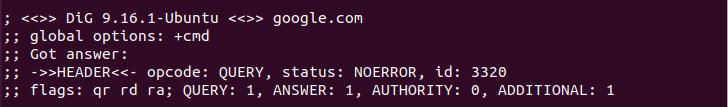
The first section of DNS lookup.
In the second section, the OPT PSEUDOSECTION shows the advanced data that is used, Extension System for DNS (EDNS), and UDP shows the UDP packet size. The question section shows the query data that the dig command sent where IN refers to the Internet and A refer to the address record we required.
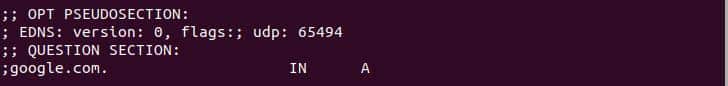
The second section of DNS lookup.
The third section shows the answers to the requested query. The first column shows the server name that the dig command query, the second column shows a set timeframe after which the record is refreshed, the third column shows the class of query, the fourth column shows the DNS record the command query, and the last column shows the ipv4 IP address that is linked with the domain name.

The Answer section of DNS lookup.
The final section shows the metadata or statistics of the query

The final section of DNS lookup.
Querying Domain ‘AAAA’ Records.
In order to query DNS records, we need to specify the record type in the command. We can shorten the output by using the +shorts, following is the output of how it worked.
$ dig +short google.com AAAA
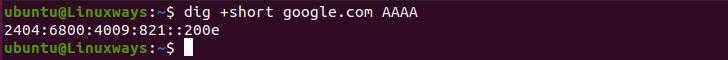
AAAA record output.
Querying Domain ‘NS’ Records Displaying Only Answers
In the following example, we have used +noall will clear all display flags which doesn’t give any output, and using the +answer option will output the answer section only.
$ dig google.com ‘NS’ +noall +answer
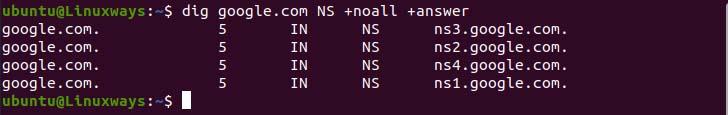
Ns record output
Querying Multiple DNS Records.
We can query multiple DNS Records using the dig command. In the example, we will query A records and TXT records using dig.
$ dig google.com +nocomments yahoo.com +noall +answer

Querying multiple records.
Querying Domain ‘MX’ Records
The MX refers to a Mail exchange that directs email to a mail server. In the command below we use the +nocomments option to exclude the comments. To lookup, the MX record specifies the record type to MX in the command.
$ dig google.com MX +nocomments
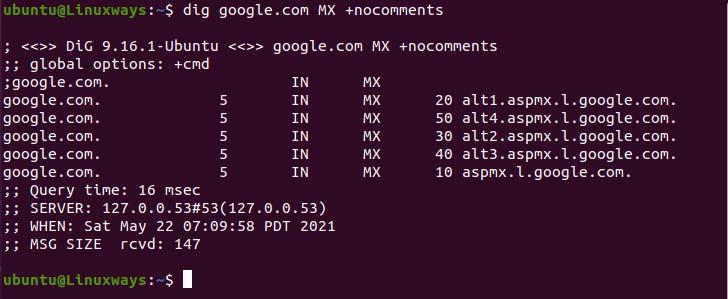
MX record output.
Querying SPF Record
The Sender Policy Framework (SPF) is used to indicate authorized hosts for sending mail to the domain in mail exchange. In the following example, we can see the SPF record of the domain in the underlined section.
$ dig google.com TXT +noall +answer
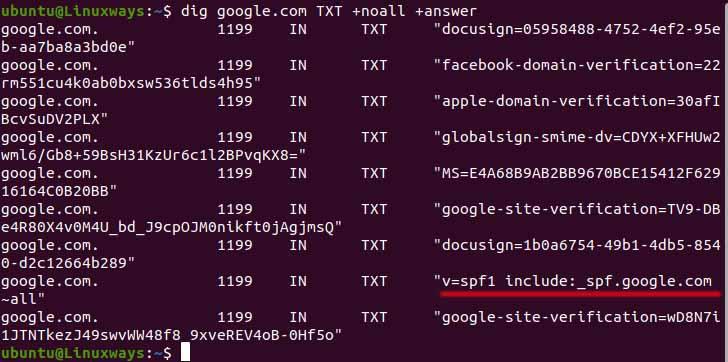
SPF Record lookup
DKIM Records Lookup
For querying DomainKeys Identified Mail (DKIM) we need the selector. It provides a digital signature and encryption key that authenticates email messages.
You need to find out the selector of the domain. If you look at the details of an email sent from google/gmail, you can find out the selector for google. Similarly, you can find other domain selectors. For querying it we have to execute the command as below. In the output, we can view the DKIM signature published in their DNS record.
$ dig txt 20161025._domainkey.google.com
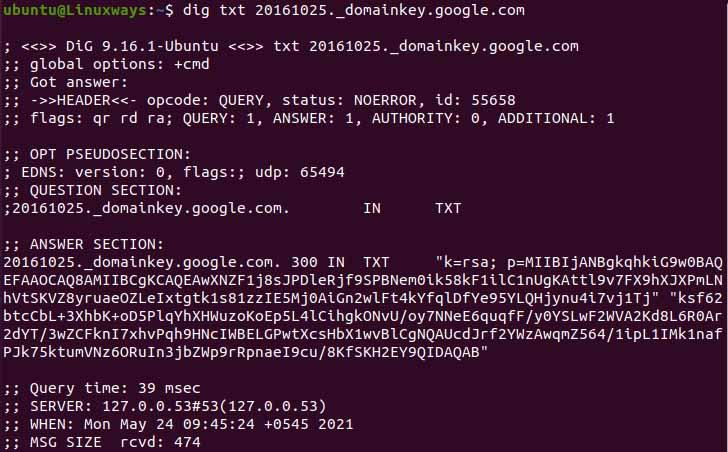
DKIM lookup
DNS Reverse Lookup
To look up reverse DNS we need to use the -x option along with the server IP address. In the following example, we use google IP address to lookup it’s reverse DNS.
$ dig -x 142.250.182.238 +short
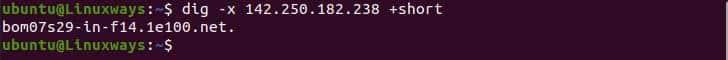
Reverse DNS lookup.
Conclusion
In this article, we have learned how to query various DNS records using the option provided by the dig command. I hope this article helps you in querying different DNS records.