Being an IT professional, it’s challenging to get up to date with security vulnerabilities and threats. System patch updates, server, and network hardening are the most crucial factors to prevent security threats. Hardening Linux servers and network devices are important to reduce IT vulnerabilities and protect from a system compromise. In this article, we will learn some best practices used for Linux server hardening. For the demonstration purpose, CentOS/RHEL server is being used so that some configurations might be different on other Linux distributions.
Update Linux Server
It’s necessary to keep your system up to date. There might be security patch updates for vulnerable components. Run the following command to update the system.
$ yum update -y
Enable and configure firewall
Most of the Linux server comes with a firewalld package installed. Make sure that the firewalld is running in the system. In the Linux system, firewall-cmd command-line utility tool can be used to configure the firewall rules.
Start and enable firewall service
$ systemctl start firewalld
$ systemctl enable firewalld
To add specific services and ports, use the following syntax
$ firewall-cmd --add-service=http --permanent (Allow http service)
$ firewall-cmd --add-port=8000/tcp --permanent (Allow specific port)
To reflect the changes, reload the firewall.
$ firewall-cmd --reload
Block USB drives
In a Linux system, USB storage can be restricted by creating a configuration files under /etc/modprobe.d/ directory.
Create a configuration file
$ touch /etc/modprobe.d/usb_block.conf
$ echo “install usb-storage /bin/false” > /etc/modprobe.d/usb_block.conf
Remove unwanted users and groups
Some users and groups are already added to the system by default which is not needed. Remove such users and groups.
$ userdel postfix
$ groupdel postfix
$ userdel games
$ groupdel games
Search of such users and groups and delete if not needed.
Remove unwanted packages
Some packages are already installed by default in the Linux system. For instance, postfix comes by default, and service starts up when the system is up. Identity such services and remove them
$ yum remove postfix -y
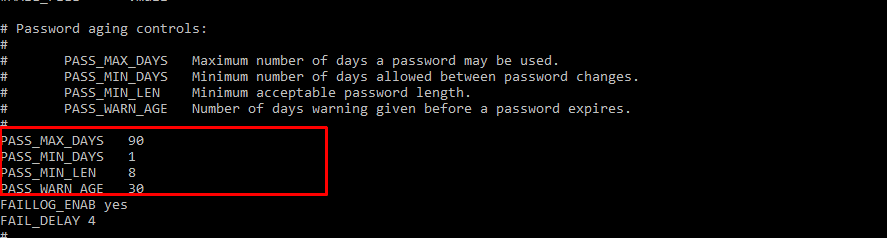
Configure password policy
In the Linux machine, the password policy is specified in the /etc/login.defs file. Make changes in the password policy parameters as follows.
PASS_MAX_DAYS 90 PASS_MIN_DAYS 1 PASS_MIN_LENTH 8 PASS_WARN_AGE 30
Example:
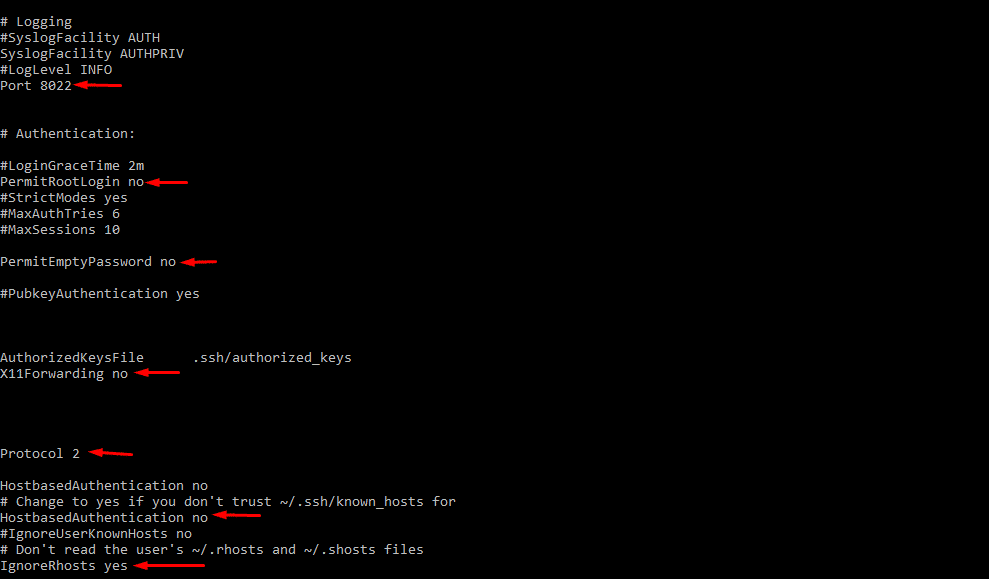
Configure SSH
To prevent unauthorized ssh access and attacks, make the following changes in /etc/ssh/sshd_config file.
# Set the custom ssh port Port 8022 # Prevent from root login PermitRootLogin no # Restrict Empty password PermitEmptyPasswords no # Restrict host-based authentications HostbasedAuthentication no IgnoreRhosts yes # Use ssh protocol 2 Protocol 2 # Disable tools that have GUI X11Forwarding no
Check the configuration using the following command.
$ sshd -t
Restart ssh service
$ systemctl restart sshd
Umask
Some files require umask hardening.
$ sed -i -e 's/umask 022/umask 027/g' -e 's/umask 002/umask 027/g' /etc/profile
$ sed -i -e 's/umask 022/umask 027/g' -e 's/umask 002/umask 027/g' /etc/csh.cshrc
$ sed -i -e 's/umask 022/umask 027/g' -e 's/umask 002/umask 027/g' /etc/init.d/functions
$ sed -i -e 's/umask 022/umask 027/g' -e 's/umask 002/umask 027/g' /etc/bashrc
Disable core dump
Core dump stores information of an executable program. It can be used to determine why the program was aborted. Core dump also can be used to retrieve confidential information from a core file. Use the following command to disable core dump.
$ echo “* hard core 0” >>/etc/security/limits.conf
Use system auditing tools
The use of security tools makes it easy to identify system glitches. One of the free and open source tools is lynis which can be used to perform a regular audit of the system. Any findings are shown on the screen and also stored in the log file.
Install the tool
$ yum install epel-release -y
$ yum install lynis
Audit the system using the command below
$ lynis audit system
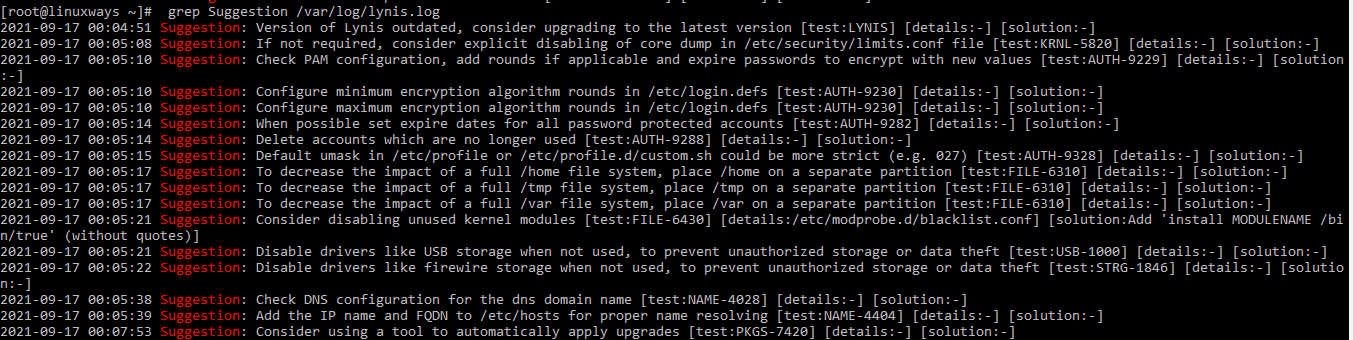
There will be suggestions and warning results stored in the log file. Run the following command to see the result and solve accordingly.
$ grep Suggestion /var/log/lynis.log
Output:
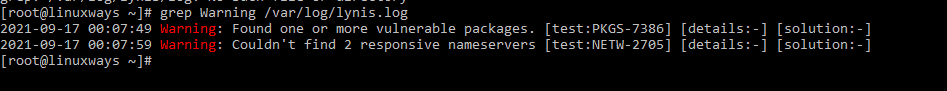
$ grep Warning /var/log/lynis.log
Conclusion
In this article, we learned some best practices to harden Linux systems. If you have any tips and tricks to secure a Linux server, do not forget to leave a comment in the box below.