In a world of constantly evolving cyber threats, securing your webserver should be top-of-the-mind concern. One of the easiest ways of boosting your web server’s security is by securing it with an SSL certificate. The encrypts the traffic exchanged between the web server and users’ browser and prevents hackers from eavesdropping and intercepting confidential information such as usernames and passwords.
Let’s Encrypt is a free and automated certificate authority that helps you to set up a secure HTTPS server using a free SSL certificate with a shelf life of approximately 90 days. In this guide, we will walk you through the process of securing your webserver using Let’s Encrypt SSL certificate.
Requirements
As we get started, we assume that you already have the Apache webserver stack installed on your Rocky Linux 8. If not, check out this guide on how to install LAMP server on Rocky Linux 8. The first step is a walkthrough of how to install Apache HTTP webserver.
Additionally, ensure that you have a valid domain name pointing to your server’s Public IP address. For this guide, we will be using the domain name called linuxtechgeek.info.
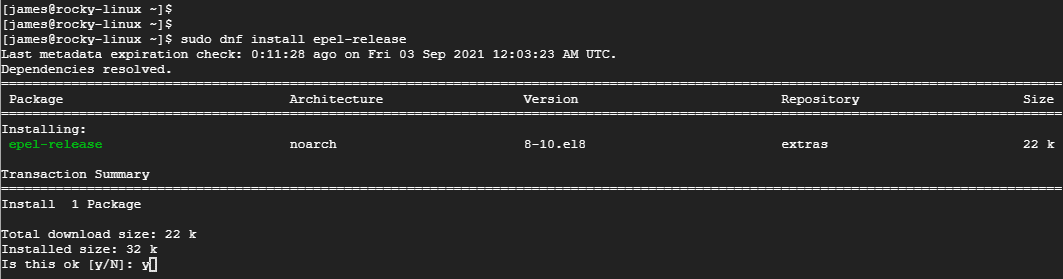
Step 1: Install EPEL repository
Right off the bat, we will start with the installation of EPEL ( Extra Packages for Enterprise Linux ). This is a repository from Fedora that provides additional packages for RHEL-based systems.
So, run the command show.
$ sudo dnf install epel-release
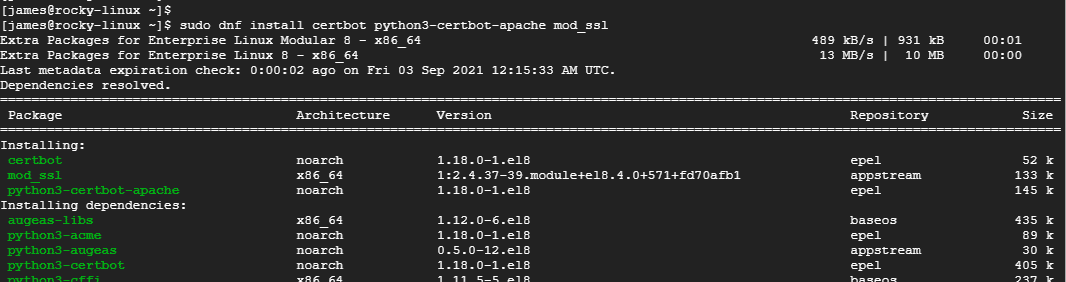
Step 2: Install Certbot
Once EPEL is installed, go ahead and install certbot , the apache module for certbot and mod_ssl which is a module that provides cryptographic features for Apache.
$ sudo dnf install certbot python3-certbot-apache mod_ssl
After the installation of the packages, restart the Apache HTTP web server.
$ sudo systemctl restart httpd
In addition, ensure that the webserver is running:
$ sudo systemctl status httpd
Step 3 : Create virtualhost file
The next step it configure an Apache virtual host file. This is a configuration that will serve our domain’s web content and will be used by certbot to facilitate the installation of Let’s Encrypt.
So, create a folder for your website. In this case, I will create a directory for linuxtechgeek.info which is my domain name pointed to the IP of my webserver.
$ sudo mkdir -p /var/www/linuxtechgeek.info
Assign the directory ownership to Apache user.
$ sudo chown -R apache:apache /var/www/linuxtechgeek.info
Next, create a virtual host file in the /etc/httpd/conf.d directory.
$ sudo vim /etc/httpd/conf.d/linuxtechgeek.info.conf
Paste the configuration shown and be sure to replace linuxtechgeek.info with your own domain name
<virtualhost *:80> ServerName linuxtechgeek.info ServerAlias www.linuxtechgeek.info DocumentRoot /var/www/linuxtechgeek.info ErrorLog /var/log/httpd/linuxtechgeek.info-error.log CustomLog /var/log/httpd/linuxtechgeek.info-access.log combined </virtualhost>
Save and exit the configuration file. Then restart Apache webserver.
$ sudo systemctl restart httpd
Let’s now obtain the SSL certificate.
Step 4 : Obtain the SSL certificate
Finally, to install Let’s Encrypt using Certbot, run the following command:
$ sudo certbot --apache
This walks you through a series of steps to configure the SSL certificate, provide your email address, read and agree the terms of service and choose which names you would want to activate HTTPS on.
Certbot will detect your virtual host configuration and request the Let’s Encrypt SSL certificate for all of them.
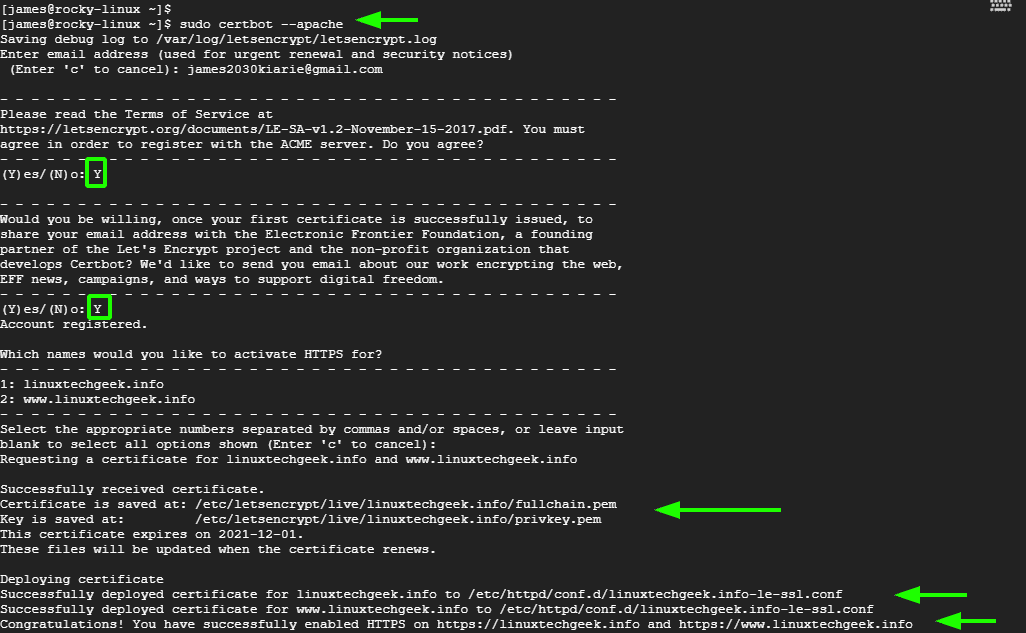
Once certbot is done applying the SSL certificate on your webserver, proceed and test the SSL settings by performing an SSL server test at SSL Labs. This is an online platform that performs a deep analysis your site’s web server.
Step 5: Configure certificate auto-renewal
As mentioned earlier, Let’s Encrypt certificate is only valid for 90 days, after which you will be required to renew it. You can renew the certificate manually a day before the expiration using the command:
$ certbot renew
A better approach would be to set up a cron job what will automate the certificate’s renewal process. So, open the crontab file.
$ crontab -e
Add this line at the very end of the file and save the changes.
0 0 * * * /usr/bin/certbot renew > /dev/null 2>&1
And it’s a wrap. Hopefully you are now at ease securing your Apache webserver with Let’s Encrypt SSL certificate.