Unbound is a recursive, validating, very secure, and DNS caching server which is distributed free of charge under the BSD license. Unbound supports DNS-over-TLS and DNS-over-HTTPS to increase online privacy by allowing clients to encrypt their connection. Depending on your network configuration, Unbound can support both IPV4 and IPV6. The installation and configuration of Unbound in Linux distributions is quite simple and straightforward. The Unbound package is available in most modern OS’s including CentOS, Ubuntu, Fedora. Companies that use their own domain to serve applications or websites internally can utilize unbound as a DNS server. In this article, we will learn how to install and configure a Unbound server in Ubuntu 20.04.
Installation
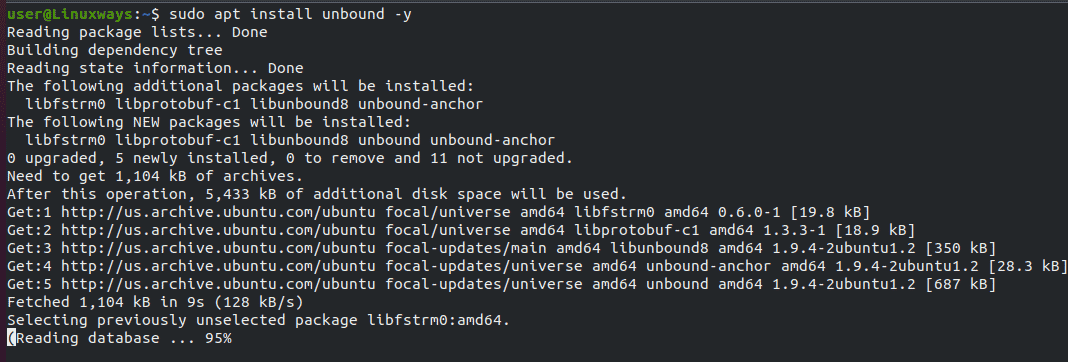
Installation of Unbound name resolution server in Ubuntu 20.04 is very simple and easy. Run the following command to install the package
$ sudo apt install unbound -y
Output:
Also, run the following command to install additional packages which we will use to check the DNS server configurations
$ sudo apt install bind-utils net-tools -y
After the installation is completed, the contents of the configuration file can be found by using the command:
$ cat /etc/unbound/unbound.conf
Output :
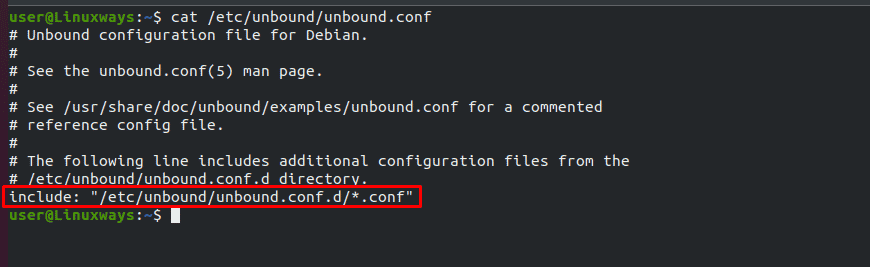
The output shows that from the unbound.conf.d directory all the .conf files will be loaded.
Lets create a new configuration file under the directory /etc/unbound/unbound.conf.d directory. In this example I have created an unbound_test.conf file. You can have your own assumption.
Open the file using the text editor and add the following sample configuration. You can modify the parameters accordingly.
$ sudo nano /etc/unbound/unbound.conf.d/unbound_test.conf
server: port: 53 verbosity: 0 num-threads: 2 outgoing-range: 512 num-queries-per-thread: 1024 msg-cache-size: 32m interface: 127.0.0.1 interface: 192.168.5.5 rrset-cache-size: 64m cache-max-ttl: 86400 infra-host-ttl: 60 infra-lame-ttl: 120 outgoing-interface: 192.168.0.2 access-control: 127.0.0.0/8 allow access-control: 192.168.5.0/24 allow username: unbound directory: "/etc/unbound" logfile: "/var/log/unbound.log" use-syslog: no hide-version: yes so-rcvbuf: 4m so-sndbuf: 4m do-ip4: yes do-ip6: no do-udp: yes do-tcp: yes
Now create a log file and assign permission to write logs $ sudo touch /var/log/unbound.log
$ sudo chown unbound:unbound /var/log/unbound.log
Restart the Unbound service the load the configuration
$ sudo service unbound restart
Use the following command to enable to service
$ sudo service unbound enable
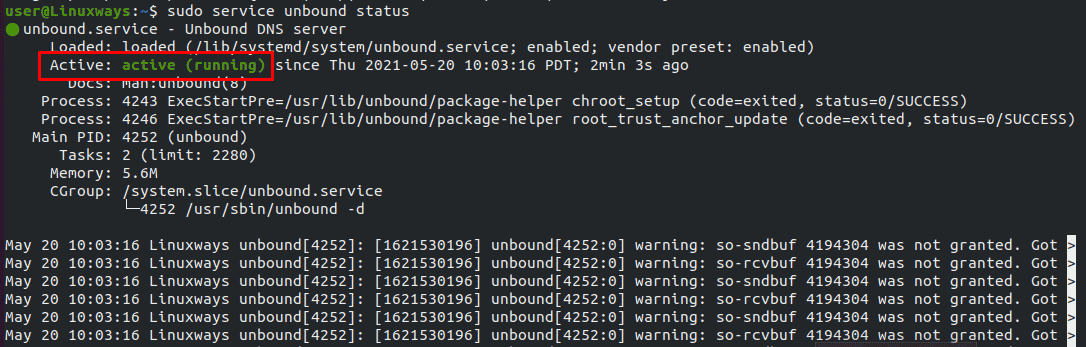
Check if the unbound service is running or not using the command:
$ sudo service unbound status
output :
Run the following command to check in which port unbound is listening to
$ sudo netstat -anlpt | grep LIST
Output:
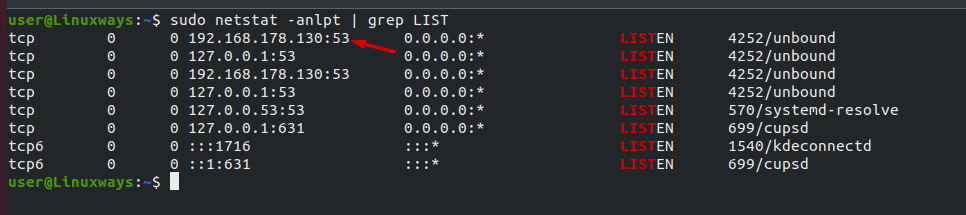
The output shows that the Unbound service is listening on port 53 to accept the requests.
Configuration file explained:
port : Listening port for Unbound
hide-version : Do not display the version of unbound
use-syslog : specify if you want to write logs in syslog
username : User, under which unbound runs
verbosity : Log level which ranges from 0 to 4 and 4 is debug log level
interface: Interfaces in which unbound requests will be listened to
outgoing interface : Interface through which internet comes
num-threads : Number of threads , recommended to specify equal number of processor core
Open the DNS port in the firewall.
Once the configuration file is created, you need to open a DNS port to allow your local LAN clients to connect to your Unbound cache-only DNS server.
$ sudo ufw allow from any to any port 53 proto tcp
$ sudo ufw allow from any to any port 53 proto udp
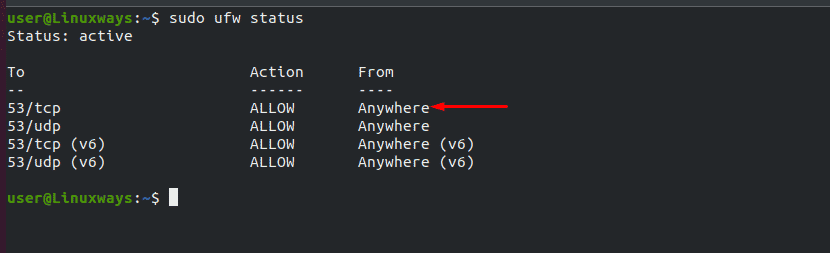
To check the firewall rule run the following command
$ sudo ufw status
Output :
Now we have come to the final point to test our new Unbound DNS server. For testing we can use the dig command which comes with the previously installed package bind-utils. Perform some DNS queries in the actual DNS server. For this example, I have queried kernel.org for testing. You can have your own assumption.
$ dig kernel.org @localhost
Output:
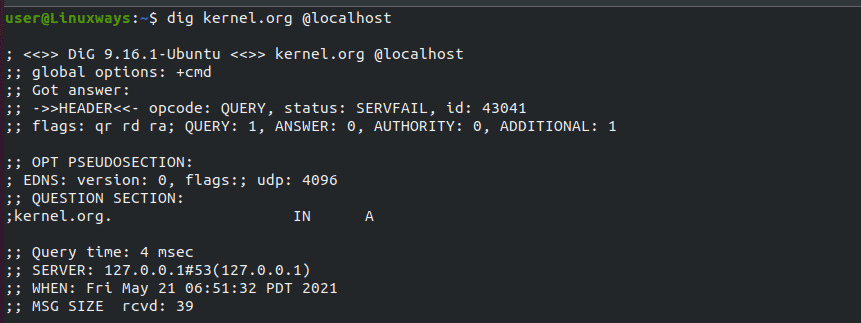
The response time is 4 msec in the first query. Since we have configured the Unbound DNS server, the query is now cached . To verify the dns cache, run the following query with the same domain name.
$ dig kernel.org @localhost
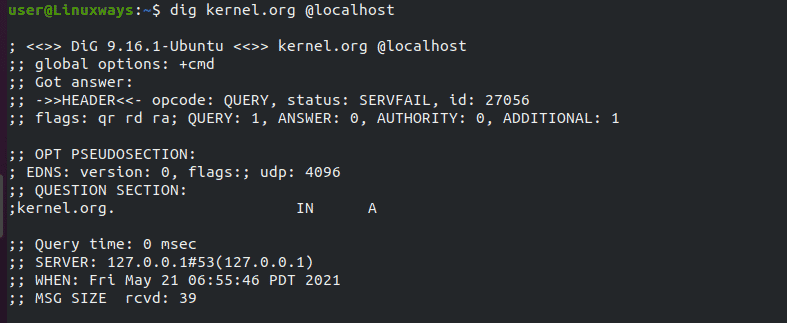
Now you can find that the query time is 0 msec.
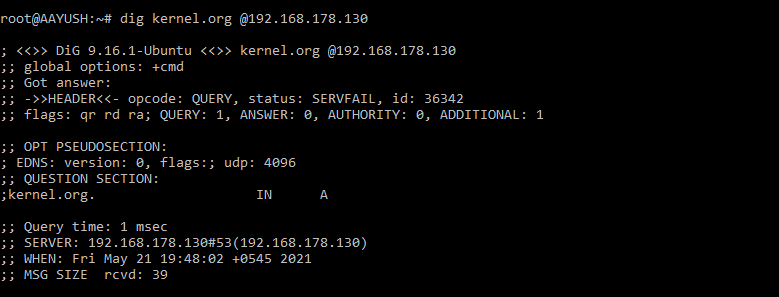
If you want to test the Unbound DNS server’s configuration from LAN clients, query the DNS response pointing to the Unbound DNS server’s IP. (In my case my Unbound DNS server IP is 192.168.178.130)
$ dig kernel.org @192.168.178.130
Optimization
The default configuration of Unbound works fine for limited users but in case there is a large number of users to be provided service then certain optimization needs to be made. Here are some optimization options which you can implement to get high performance.
num-threads: Put the equal number of CPU cores on the system, for example, put the value 4 for 2 CPUs with 2 cores each.
so-reuseport: yes In linux, this helps to improve UDP performance
outgoing-range: You can set the value large as possible depending on the number of cores.
so-sndbuf: This value can be set to a larger value 4m or 8m for a busy server.
For more details you can take reference from
https://nlnetlabs.nl/documentation/unbound/howto-optimise/
Conclusion
In the article, we have covered how to install and configure the Unbound name resolution server in Ubuntu with basic configuration. Certain tests have been performed using the dig command to check the configuration of the Unbound server. Also, we have learned about how to query DNS responses from the local LAN client using the Unbound server’s IP. Any feedback and suggestions will be highly appreciated.