SSH refers to Secure Shells that helps in operating network services like remote login to the server, file transfer, and other servers related operation securely over an insecure or secure network.
The SSH default configuration is not enough to harden the SSH channel; we need to configure the additional setting to enhance its security at full. In this article, we are going to learn 11 methods of securing your ssh server.
Disabling Root Login Over SSH Server
As the root user has access to the entire services in the server and it’s better not to risk the system allowing remote root login. It might be way too vulnerable if the password is exposed while using a brute-force attack or other hacking tool. So it is best practice to disable remote root login and stick with the regular user.
To disable the remote root login, open the sshd_config file.
$ sudo vim /etc/ssh/sshd_config
Then, set “PermitRootLogin” to no

Disable ssh root user login.
Disable Empty Password
Some Linux distributions will create users without passwords so it might be vulnerable to permit ssh connection with empty passwords for remote access. So in order to disable this service we need to set “PermitEmptyPasswords” to no in the sshd_config file.
PermitEmptyPasswords no
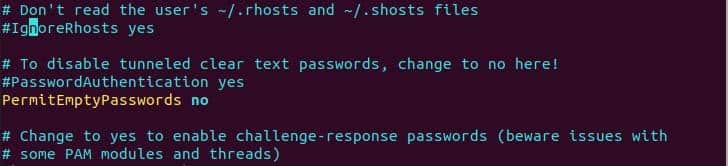
Disable empty password login.
Use Public Key Based Authentication Across SSH Protocol.
It is highly recommended to use public key-based authentication as the SSH server supports different authentication processes. The hacker attempts different hacking tools to crack down the password using various methods like brute force attack. To prevent it from happening we use public key-based authentication.
First, we need to generate a public key and private key using the ssh-keygen command. To generate the key execute the following command. In the process you will be asked where to generate the ssh key, hit enter if you want to continue with the default. Then you will be asked a passphrase that refers to the password to your ssh key, uses a strong password that is the composition of a special character, alphabet, and numbers. Once the password is set your ssh key will be generated on .ssh dir in your home directory.
$ ssh-keygen -t rsa
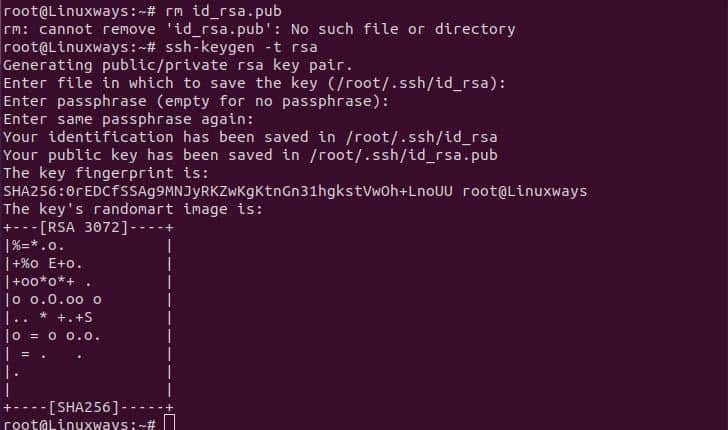
Generating ssh key pairs.
Before uploading public key, make sure you have .ssh dir in your remote server if not create one in your home dir then upload your public ssh key to the server using the following command.
$ cat .ssh/id_rsa.pub | ssh ubuntu@192.168.233.256 'cat >> .ssh/authorized_keys'
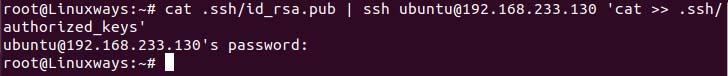
Uploading the public key to the server.
Now you can login as user ubuntu using public key over ssh protocol.
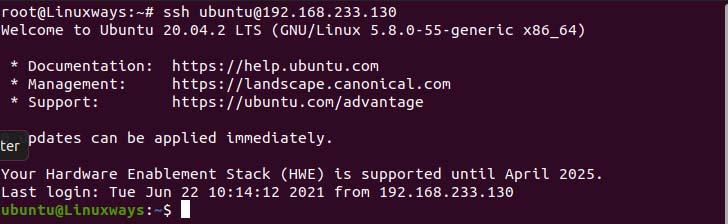
Public key based authentication.
Disable SSH Login Authentication With Password
It is highly recommended to use ssh public key authentication for remote access to the server as passwords can be exposed through brute force attacks if a strong password is not used. To disable password authentication from the SSH server set the “PasswordAuthentication” value to no.
PasswordAuthentication no
Change SSH Default Port 22.
By default, SSH runs on port 22 in the system. If we change the SSH standard port it might add an extra layer of security by avoiding unusual traffic to the open port. So, to change the port no simple, open the sshd_config file and set your desirable unused port number in the port section. Ih the following example I have set the port to 454.
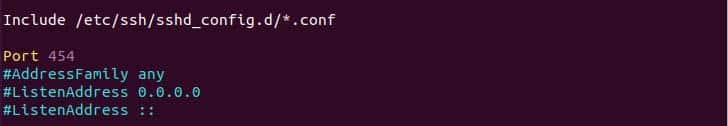
Change ssh default port.
Limit Users Login Access Using SSH.
The SSH server allows all the users to the server remotely but we can override the default setting and set only specific users to allow or deny remote access over SSH protocol. In a simple way having remote access to all system users login creating a possible way for the hacker to access our system.
To allow the specific users to login over SSH, add the following line in the sshd_config.
AllowUsers user1 user2 ubuntu
And similarly, you can restrict specific user and allow other to access over SSH by adding the following line of code.
DenyUsers root user3 user4
Enhance the use of Strong Passwords for SSH User/Key.
Usually, people often use simple passwords for their login like 123456, something123, so that they can remember passwords easily. This is why a brute force attack works perfectly as it goes dictionary wise to attempt the password check. So, to avoid that we must use a password containing special characters, uppercase and lowercase alphabet, numbers, and a minimum password length of 8 characters long.
Configure Idle Timeout Interval
Users often keep their SSH connection idle for a longer period so it will be high risk if someone tries to take over your SSH session and do as they like when users are not present at the moment. So we can set our login session timeout after a certain period of inactivity so that we need to re-login on session timeout. To set the idle timeout we need to set the “ClientAliveInterval” value in the sshd_config file. In the following example, I have set the timeout value 360 which is 6 minutes.
ClientAliveInterval 360
Use SSH Protocol 2
SSH has two variants of protocol SSH protocol 1 and SSH protocol 2, protocol 1 is the system default which is less secure than protocol 2 as protocol 2 applies bulk encryption, robust algorithms, and cryptographic checks. To switch to protocol 2 we need to add the following line in the sshd_config file.
Protocol 2
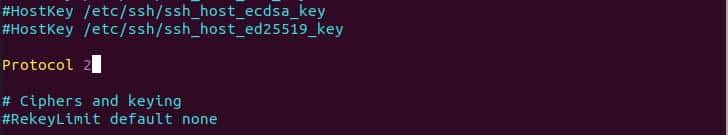
Using ssh protocol 2.
Configure a Limit for Password Attempts
We can limit the number of password attempts to ssh login so after a limited number of attempts the connection will drop which will add an extra layer of security that prevents the system from the bot attack. To achieve this we need to set the “MaxAuthTries” directive value. In the example, I have set its limit for 4 attempts.
MaxAuthTries 3

Limit the ssh login attempt.
Disable Tunneling and Port Forwarding
If you won’t be using tunneling and port forwarding service its is better to keep it disabled as a hacker might use these services to break through your system. To achieve it set the following directive value to no.
AllowAgentForwarding no
AllowTcpForwarding no
PermitTunnel no
Finally, after everything is set up don’t forget to restart your ssh server to apply the changes
$ sudo systemctl restart ssh
Conclusion
In this article, we learn some common ways of hardening SSH servers that help to avoid different security risks. I hope you like this article.