Rkhunter is the open-source security analyzing and monitoring tool that scans rootkits, local exploits, and backdoors in the Linux system. It does check for strings in kernel modules, wrong permission, hidden files, etc to enhance Linux security. It was written in Bourne Shell (sh) and compatible with almost all UNIX-derived systems.
In this article, we will install Rkhunter and scan the system for the backdoor, rootkits, and local exploits in Ubuntu 20.04 system.
Installing Rkhunter
As of Ubuntu 20.04, Rkhunter can be installed from its default repository. Execute the following apt command to install the Rkhunter package.
$ sudo apt install rkhunter -y
After executing the command you will see the following dialog requesting to set up a mail server. Then, click on the ok button. In this dialog, you can see the mail server type info.
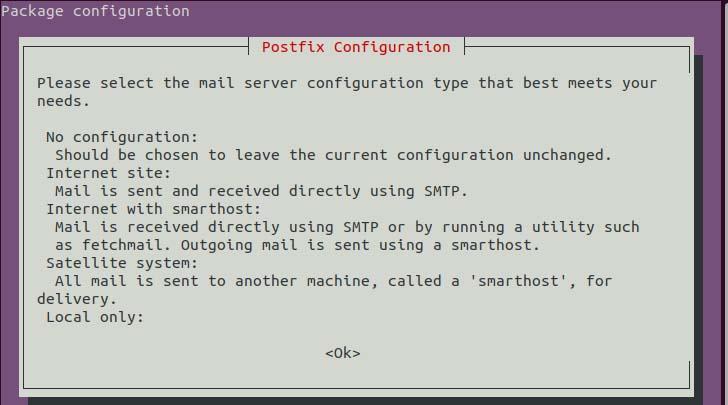
Mail server configuration wizard.
Again, you will be asked to choose the mail server as the type is defined in the initial dialog. For my setup, I will choose ‘Local only’. After you select your mail server click on ok.
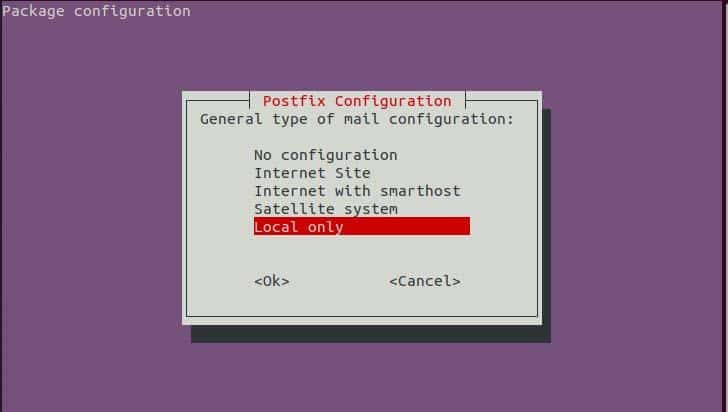
Mail server configuration wizard.
In a few minutes again you will see the dialog asking for the system mail name. If you have a mail address you can set the mail address according to description otherwise set it localhost or your server hostname. Then click on ok.
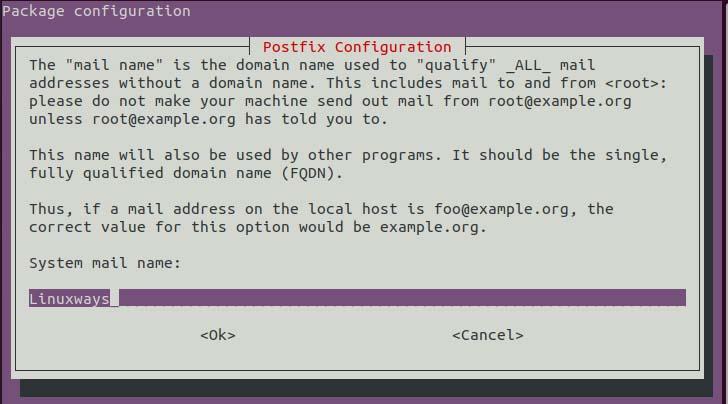
Postfix configuration.
Now, verify the installation using the following command.
$ rkhunter --version
Configuring Rkhunter
Once installation is complete we need to configure Rkhunter to be able to scan the system at the fullest. Then, open the following config file.
$ sudo vim /etc/rkhunter.conf
Now, find and update the following variable to the given value.
UPDATE_MIRRORS=1
By default, its value is set to 0 which defines don’t update to mirror files. The rkhunter mirror files are also being checked for an update if we set the value 1 during the update check.
MIRRORS_MODE=0
The MIRRORS_MODE tells the Rkhunter which mirrors are to be used when the –update or –version option is used. It takes one of the 3 options,
0 – use any mirror
1 – use local mirrors only
2 – use the remote mirror only
WEB_CMD=””
The WEB_CMD determines the command that Rkhunter uses to download files from the Internet.
Once the above configuration is set, write and quit the config file.
During Rkhunter installation its script file is appended in the cron.d Daily directory for the daily scanning and updating as the script is executed by cron regularly. So, update the configuration of the following config file to auto scan and update regularly.
$ sudo vim /etc/default/rkhunter.conf
CRON_DAILY_RUN=”true”
CRON_DB_UPDATE=”true”
APT_AUTOGEN=”true”
Once the configuration is all set you can check if the configuration is set up correctly using the following command.
$ sudo rkhunter -C
Update Rkhunter
The Rkhunter uses text data files to detect suspicious activity. So, we need to update frequently. To check for update execute,
$ sudo rkhunter --update
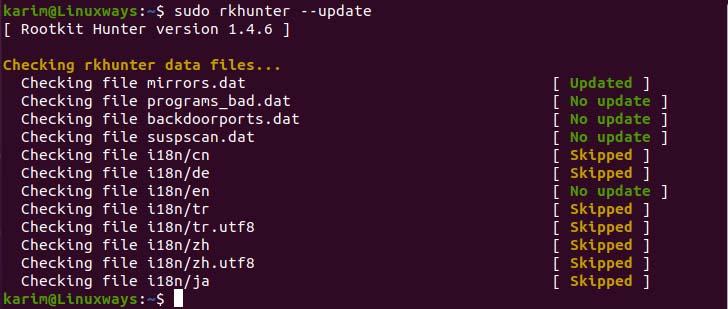
Check for rkhunter data files update.
Now, update the entire file properties databases using the following command.
$ sudo rkhunter --propupd
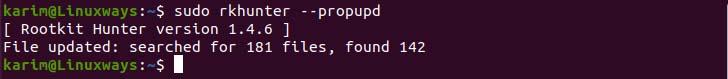
Updating data files.
Scanning System With Rkhunter
Once everything is set up you can perform a system check using rkhunter.
$ sudo rkhunter --check --sk
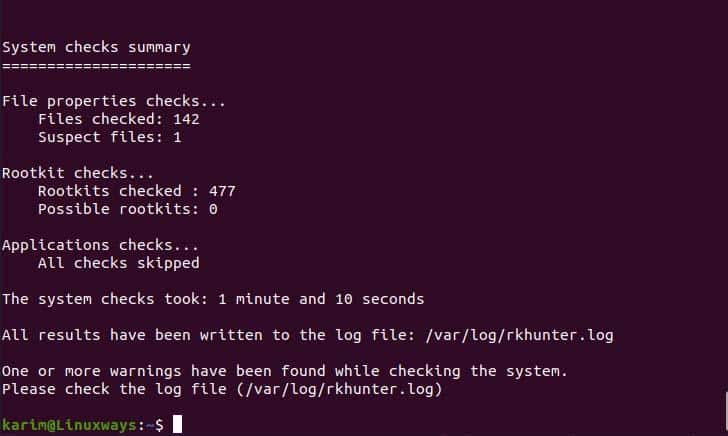
Scanning the system.
$ sudo rkhunter --check --rwo
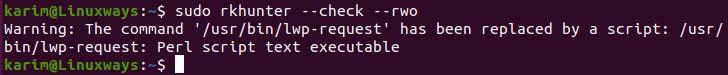
View only warnings.
In the above command –check option tell the command to scan the system, –sk option will skip option to press enter key for the continuation of the scanning, and –rwo only display warning message only
After scanning you can check the log in the following path to view the warning.
$ sudo cat /var/log/rkhunter.log
Conclusion
Till now you have learned the way to install rkhunter, configured the required configuration, and scan the system and viewing log to identify actual backdoor, rootkits, and local exploits.