Network mapper, abbreviated as Nmap, is an open-source network scanning tool that scans remote hosts and probes for a wealth of information such as open ports, OS versions, and versions of services listening on the open ports. Depending on the arguments used, Nmap also reveals underlying system vulnerabilities associated with outdated vulnerabilities based on CVSS (Common Vulnerability Scanning System). For this reason, Nmap is a valuable reconnaissance tool for penetration testing and revealing loopholes that can be exploited by hackers. In fact, it comes pre-installed in Kali and Parrot OS which are operating systems dedicated to penetration testing and digital forensics.
In this article, we highlight some of the useful Nmap commands that help you gather useful information about remote hosts.
Basic Nmap syntax
The most basic Nmap command involves scanning a single host and requires only the IP address or the hostname of the remote target as the argument.
$ nmap hostname
Or
$ nmap remote-host-ip
Let’s now delve into some Nmap use cases. In this guide, we will scan remote hosts using Kali Linux.
Scan a single remote host
Scanning a single host is pretty straightforward. All you need is to pass the remote host IP address or domain name as the argument. For example,
$ nmap 192.168.2.103
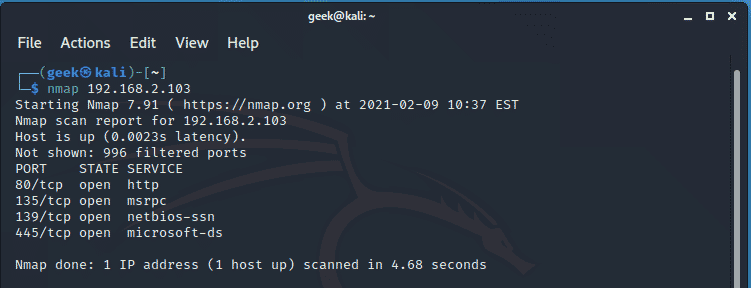
The Nmap scan report includes details such as the open ports, state of the port, and the services listening on the ports.
Scan multiple remote hosts
In a scenario where you have multiple remote hosts, simply pass their IP addresses on a single line as shown.
$ nmap 192.168.2.103 192.168.2.1
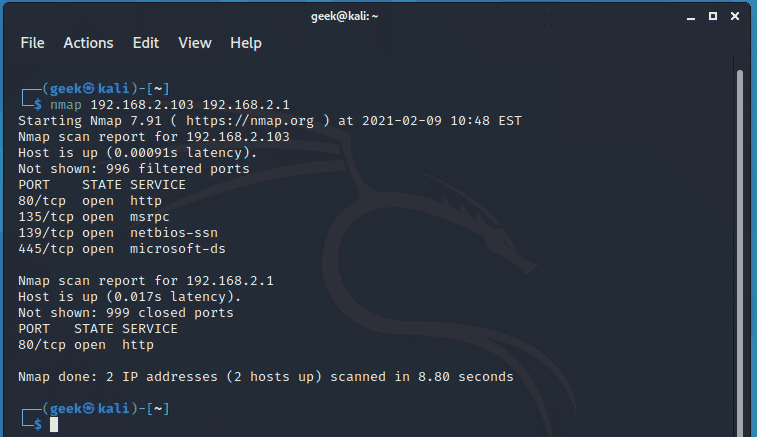
If you wish to scan consecutive remote host IP address, simply suffix the address as follows:
$ nmap 192.168.2.1,2,3,4
The command above scans the remote hosts 192.168.2.1, 192.168.2.2, 192.168.2.3, and 192.168.2.4
Scan a range of remote hosts
If you have remote hosts in a range of IP addresses, you can specify the range separated by a hyphen.
$ nmap 192.168.2.100-105
This will scan all the remote hosts from 192.168.2.100 to 192.168.2.105 range.
Scan a subnet
You can scan an entire subnet by making use of the CIDR notation. For instance, the command below scans all the remote hosts in the 192.168.2.0 subnet.
$ nmap 192.168.2.0/24
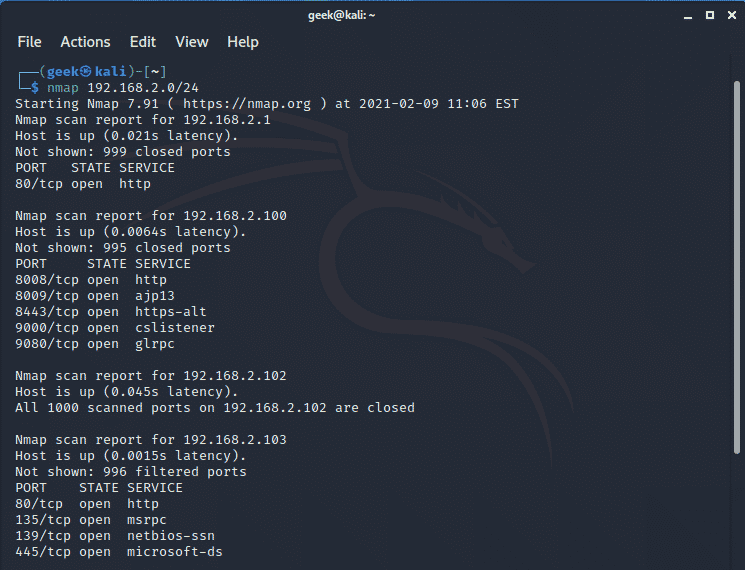
Port scanning using Nmap
You can instruct Nmap to explicitly scan open ports on a target host using the -p flag followed by the port number. In the example below, we are scanning for port 80 on the remote host.
$ nmap -p 80 192.168.2.100
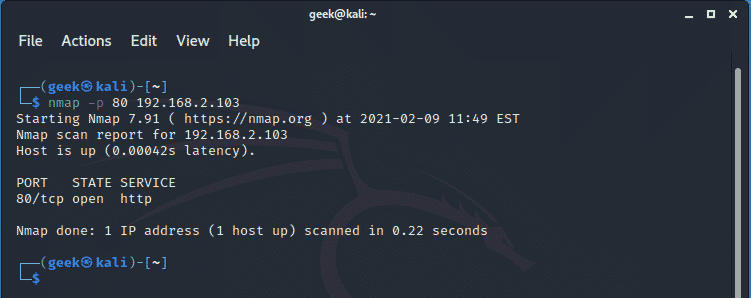
To specify multiple ports, you can list them using commas as shown below.
$ nmap -p 80,135,139 192.168.2.100
To scan all open ports on a target, use the –open flag. Here, we are scanning Metasploitable Linux which is an intentionally vulnerable virtual instance for penetration testing.
$ nmap --open 192.168.2.107
Scan for active remote hosts
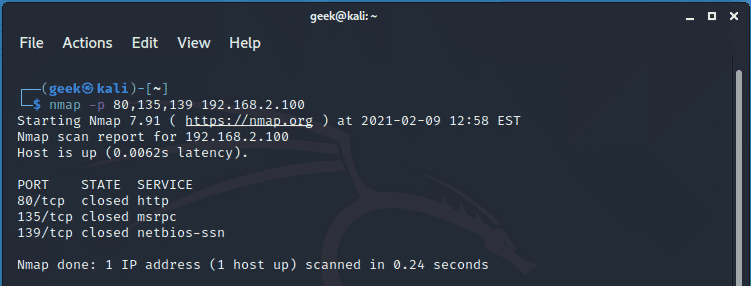
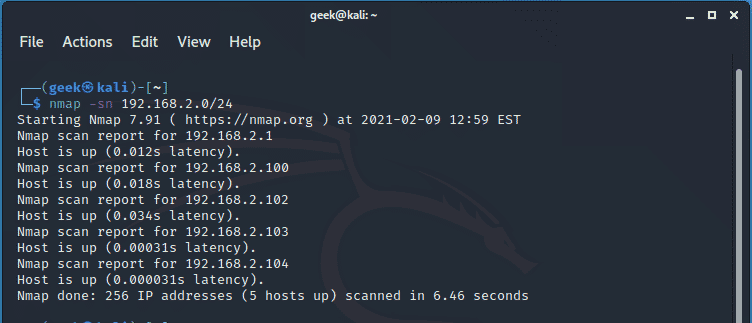
If you just want to know which remote hosts are alive in your subnet, pass the -sn flag as shown. The output will be nothing fancy, just a brief summary of the active hosts.
$ nmap -sn 192.168.2.0/24
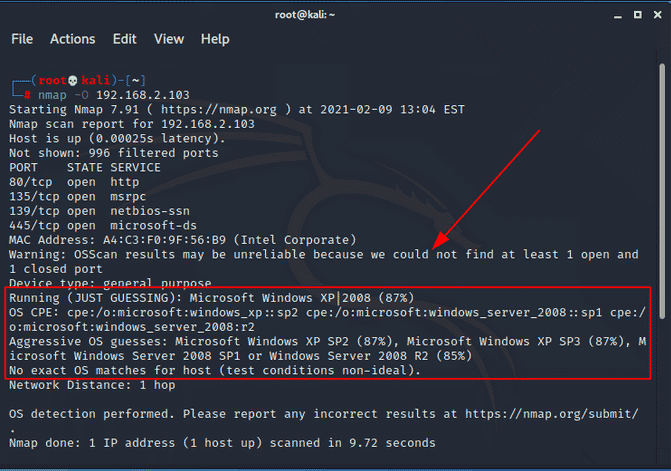
OS fingerprinting
The -O flag enables you to even detect the host’s operating system to a certain degree. However, this does not give you the exact version of the target’s OS. In the example below, we are scanning a host that runs on Windows 10, but the OS guesses suggest that the remote host is likely to be Windows XP SP2 or Windows Server 2008 / 2008 R2.
# nmap -O 192.168.2.103
Service detection
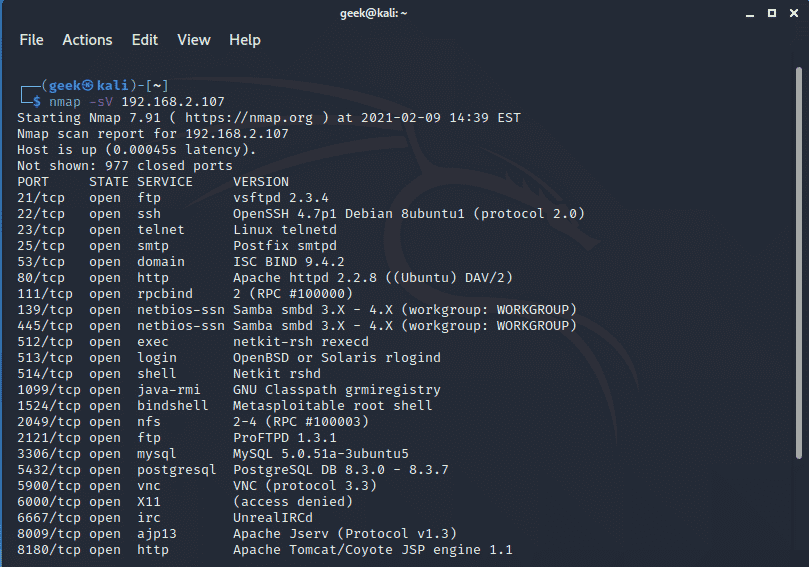
You can get down to the nitty-gritty of the services listening on associated ports using the -sV flag. Common services include SSH ( port 22), HTTP ( port 80), and DNS ( port 53 ). Service detection is one of the most critical scanning tasks. It helps in pointing out outdated service versions that may leave the system prone to exploits and attacks.
$ nmap -sV 192.168.2.107
Perform a stealth scan using Nmap
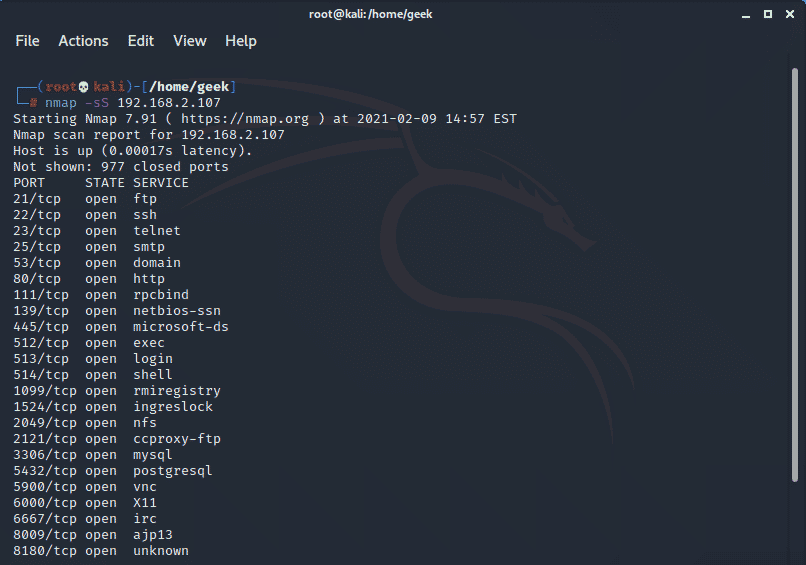
A stealth scan, also abbreviated as SYN scan, is an unobtrusive kind of scan that quickly scans multiple ports within the shortest time possible. A SYN packet is sent to the remote target and when the response is received, Nmap is able to report on whether the port is open, filtered, or closed.
$ nmap -sS 192.168.2.107
Perform a detailed scan
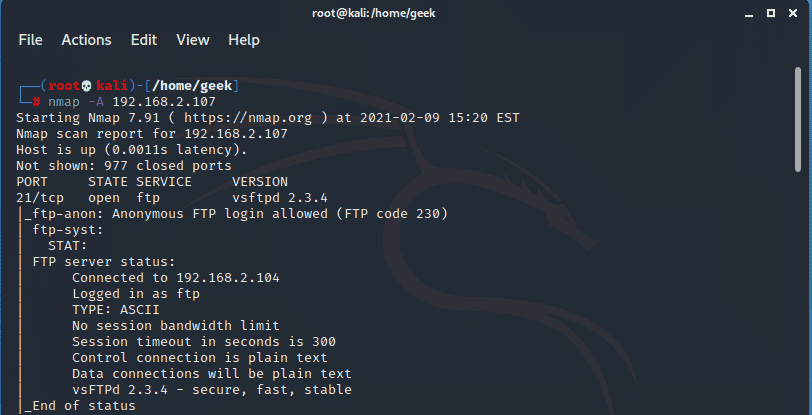
The -A flag performs a deep inspection of the remote target’s ports and gives finer details about the version of running services and also points out any vulnerabilities with the service.
$ nmap -A 192.168.2.107
Perform firewall identification
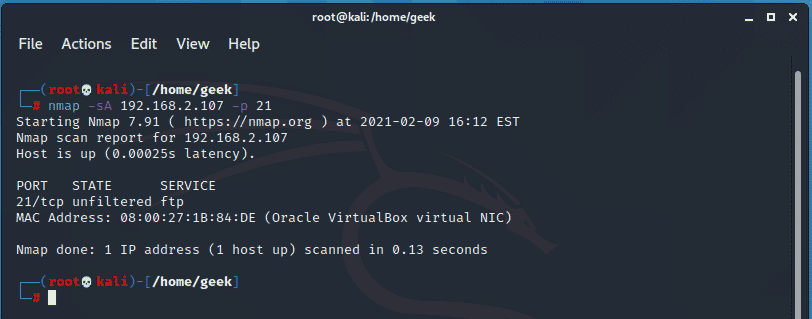
The Nmap can also perform firewall identification to check if the ports are filtered or not. The -sA option checks whether the firewall is enabled and needs to be combined with the -p flag and port number. ‘Unfiltered’ implies that the port is not behind a firewall while ‘filtered’ means it’s opened on a firewall that is enabled.
$ nmap -sA 192.168.2.107 -p 21
Scan TCP or UDP protocols
If you want to scan TCP ports only, use the -sT flag as shown.
$ nmap -sT 192.168.2.107
If you choose to scan to reveal UDP protocols only, use the -sT option.
# nmap -sU 192.168.2.107
Using Nmap scripts to scan vulnerabilities
Nmap Scripting Engine, abbreviated as NSE, provides Nmap scripts that extend Nmap’s functionalities. Nmap scripts are mostly used in probing vulnerability and malware detection. These scripts come preinstalled on Kali Linux and are located in the /usr/share/nmap/scripts path. They have a unique .nse file extension.
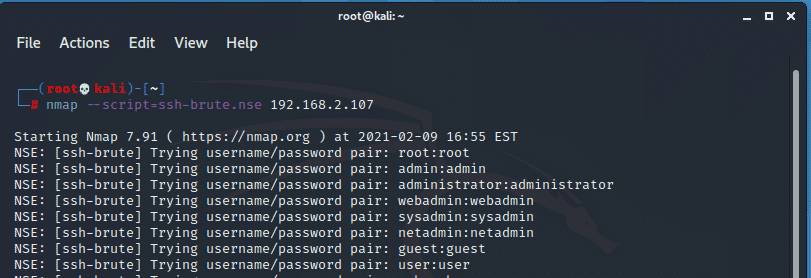
For example, to check if a remote host can be brute-forced using SSH use the Nmap script below.
$ nmap --script=ssh-brute.nse 192.168.2.107
Save Nmap scan results
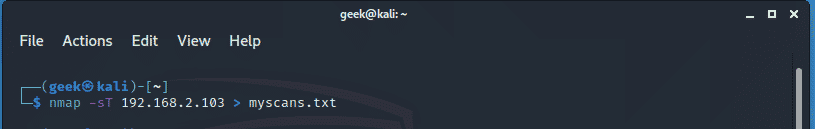
If you are in a hurry and want to save the results of a Nmap scan for later review, you can use the redirection greater than sign > as shown.
$ nmap -sT 192.168.2.103 > myscans.txt
Scan hosts from a text file
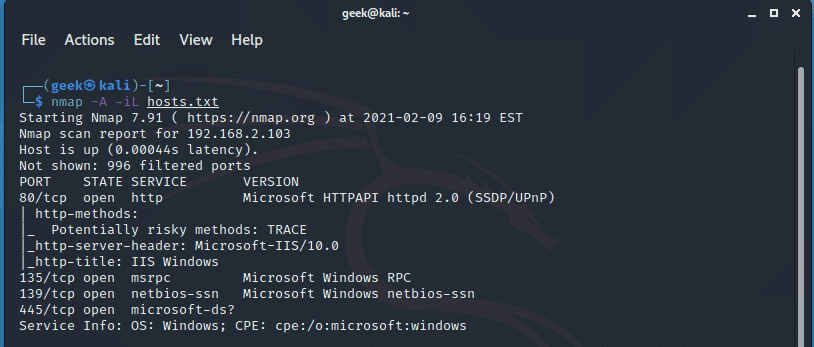
Alternatively, you can scan your remote hosts which are defined in a text file. To read the file, use the –iL option.
$ nmap -A iL hosts.txt
Conclusion
We have listed 15 Nmap commands that you can use to get started with scanning your remote hosts. There are hundreds upon hundreds of Nmap commands and Nmap scripts that are used for scanning hosts and probing for any vulnerabilities. We hope you now have the basics of Nmap and running commands to reveal information about remote targets. If you are considering scanning an organization’s assets, ensure that you seek permission from the management lest you get into trouble.