Firewalld is a firewall management tool that is used to allow or deny connection to the Linux system. It provides a set of rules to control the inbound traffic. Firewalld acts as the front end for the Linux kernel Netfilter.
The permanent configuration is loaded from XML files in `/usr/lib/firewalld` or `/etc/firewalld`
In this article, we are going to install and use firewalld. Also, I am going to show you how to use rich rules.
Install firewalld in CentOS / RHEL
Firewalld comes with the basic installation of Redhat or Centos. If there is not, you can install it in the following ways.
On RHEL 7.X or centos 7.X install by,
$ sudo yum install firewalld -y
On RHEL 7.X or centos 8.X install by,
$ sudo dnf install firewalld -y
To start the service,
$ sudo systemctl start firewalld
To enable the firewalld service,
$ sudo systemctl enable firewalld
Check the status of firewalld,
$ systemctl status firewalld
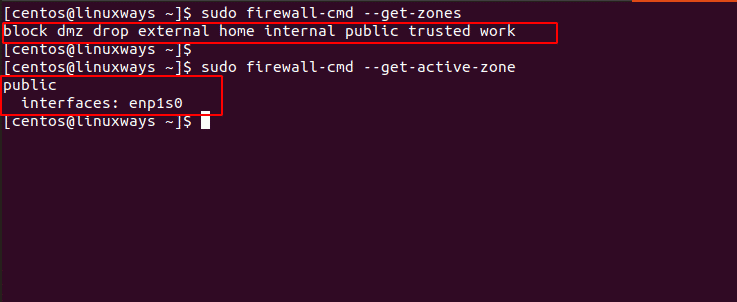
Firewalld comes with different predefined zones also known as level of trust. Zones are basically managed groups that have a set of rules. However, the rules are not predefined. For example, you can set a ‘public’ zone which contains public hosting ports, while ‘home’ zone allows ssh connections. To list zones in firewalld use following command,
$ sudo firewall-cmd --get-zones
To see active zone among the zones use,
$ sudo firewall-cmd --get-active-zone
Now, let’s add some ports to allow traffic into our system. To add a tcp port you have to type the following. Remember to add –permanent option otherwise, your rule will not be persistent on reload / restart of firewalld.
$ sudo firewall-cmd --add-port=443/tcp --permanent
Similarly, you can also allow UDP port,
$ sudo firewall-cmd --add-port=161/udp --permanent
You can also allow services such as DNS, HTTP. It will allow the default port of the service. For example,
$ sudo firewall-cmd --add-service=http --permanent
After you add the port / Reload firewall service to take into an effect
$ sudo firewall-cmd --reload
Verify using,
$ sudo firewall-cmd --list-all
Remember: When you don’t add any zone, the rule will be added to the ‘public’ zone by default.

To remove port from firewalld you can use,
$ sudo firewall-cmd --remove-port=443/tcp --permanent
To remove service from firewalld you can use,
$ sudo firewall-cmd --remove-service=http --permanent
Remember to reload the firewall after you add or remove the port/services.
Rich rules
Rich rules provide more granular options to firewall rules. They are used to configure port forwarding, rate limiting, logging etc.
For example, to accept ssh connection form a single IP say, 192.168.10.25 you should add a rich rule by specifying IP version, source address, port, protocol.
$ sudo firewall-cmd --permanent --zone=public --add-rich-rule='rule family="ipv4" source address="192.168.10.25/32" port protocol="tcp" port="22" accept'
In similar way, you can drop all the ip source of a entire network not to allow 22 port as below,
$ sudo firewall-cmd --permanent --zone=public --add-rich-rule='rule family="ipv4" source address="192.168.15.0/24" port protocol="tcp" port="22" drop'
To allow new IPv4 connections from address 192.168.0.0/24 for service tftp and log 1 per minutes using syslog you can do,
sudo firewall-cmd --permanent --zone=public --add-rich-rule=’rule family="ipv4" source address="192.168.0.0/24" service name="tftp" log prefix="tftp" level="info" limit value="1/m" accept’
Uninstall firewalld
If you like to remove firewall demon from CentOS / RHEL then stop the running service,
$ sudo systemctl stop firewalld
On RHEL 7.X or Centos 7.X
$ sudo yum remove firewalld -y
On RHEL 8.X or Centos 8.X
$ sudo dnf remove firewalld -y
Conclusion
We hope this article helps you to increase the security of your Linux system. Note that the host-based firewall like firewalld is recommended by compliances like PCI DSS.
Thank you for reading.
Pratik Gautam is a system engineer on Cloud Computing, Linux system, and Amazon Web Services. He is a certified Linux administrator and a tech enthusiast having more than three years of experience at fintech and media house of Nepal. He has Bachelor’s degree in computer science and information technology from Tribhuvan University. He always believes in sharing IT knowledge and adopting new technology.