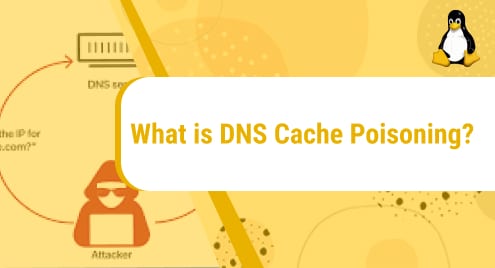
DNS poisoning is a very deceptive cyber threat. It is a type of cyberattack, which exploits server vulnerabilities to divert traffic away from legitimate servers to fake or malicious ones. Once you’ve navigated to the fake page, despite being the only one who can solve it, you may struggle while resolving the issue. You need to know exactly how everything works to protect yourself from it.
Without completely understanding how your computer connects to the Internet and then to your desired websites, a DNS poisoning attack may deceive you into thinking that the website itself has been hacked. Though in some cases, it may just be your device, if the attack is carefully planned the extent of the damage can be very extensive. So, if you want to know more about the details of this thread, keep on reading.
What is DNS?
In the first paragraphs, we’ve talked about DNS multiple times, but what exactly is DNS? DNS stands for “Domain Name System”. Consider it to be like a huge directory for the Internet.
When a user types in the URL/domain name of their desired website in their browser window (e.g., www.youtube.com into google chrome), a DNS would then translate the human-friendly URL into machine-friendly IP addresses (e.g. 192.168.0.1). These IP addresses are uniquely assigned to each device connected to the internet. This part is also known as DNS resolution.
Simply put, to locate the web page and its resources requested by the user a DNS takes the URL, converts it into an IP address, accesses the resources and displays them on the web browser.
Now before we understand what is DNS poisoning in detail, we need to understand what is a DNS cache.
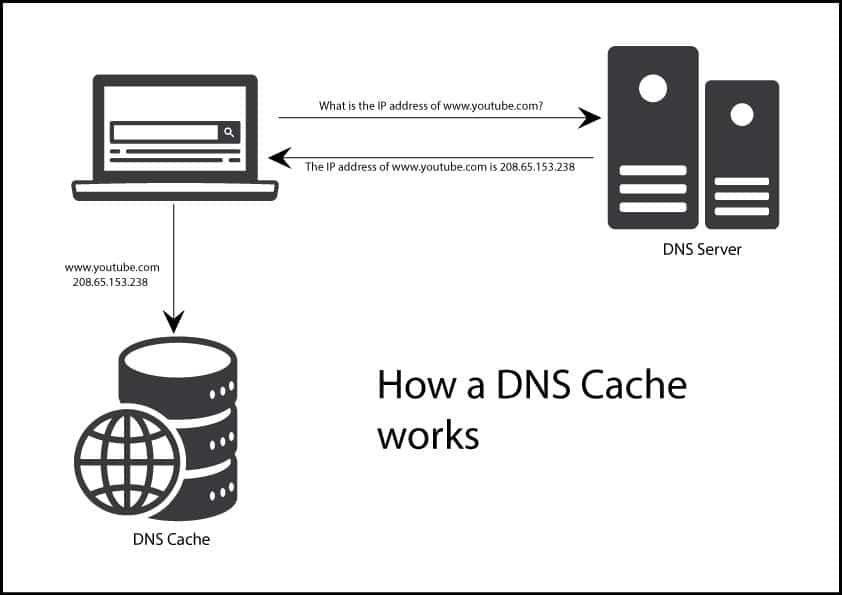
DNS cache
Caching or DNS caching is when the DNS resolver temporarily stores the responses for IP address queries in a cache.
Through caching a DNS system responds to queries faster, without having to communicate with various servers involved in the resolution process. Generally, the data can be cached in multiple locations for a specific period of time (also known as time-to-live)
How is a DNS cache poisoned?
A DNS cache is poisoned when an external/malicious actor feeds incorrect information into the DNS cache, forcing the user’s browser to return with an incorrect response. Usually, this response redirects the user to a website other than the one the user intended to access. As this happens, spyware, worm or any other kind of malware can be installed on the user’s machine from the malevolent location.
A DNS server can not verify data during resolution, which means that the incorrect information can remain in the cache until the time-to-live expires. Though this poisoning cannot disconnect the real website from its IP address, users will continue to be redirected to the rogue website as long as the DNS cache is poisoned.
Due to the longstanding and inherent weaknesses of the DNS, it’s pretty easy for attackers to infiltrate a DNS lookup for malicious purposes. DNS was built for a smaller internet, and with the principle of trust since, at that time there was no reason to expect anyone would try to propagate false DNS information.
How to prevent DNS cache poisoning?
It is very hard to eliminate the threat of a poisoned DNS cache because even if the infected server is completely cleaned, individual user devices can still return to the malicious sites and cause problems for their users. Yet, it is possible to enhance the chances of avoiding a cache from being poisoned. Prevention can be considered a two-fold responsibility for the end-users as well as the website owners and the DNS service providers.
For website owners and DNS service providers
– Use the DNSSEC (DNS Security Extensions) protocol, which implements a hierarchical digital signing policy at each level to prevent such poisoning attacks.
– Deploy spoof detection tools to verify if a request has been answered by the accurate DNS server, and identify if a server has been hijacked through the DNS response.
– Implement E2E (end to end) encryption to make their systems more resilient. It will enable the system to send such encrypted DNS requests that only the planned recipients can decrypt.
For end-users
– Don’t open unknown links.
– Use a VPN (Virtual Private Network) if and when possible.
– Regularly scan your devices for malware including viruses, worms, keyloggers and trojans.
– Regularly flush your DNS cache.
Conclusion
Throughout the article, you’ve understood what is a DNS cache poisoning attack and how can you help prevent it. It is imperative that you stay vigilante to prevent such attacks, otherwise you might end up with your data at risk, leave your devices at the risk of malware infection or forced censorship, and even the attacker might halt your security update leaving you vulnerable to a plethora of other attacks.
As always, if you have any queries or concerns, feel free to leave a comment down below and we will try to address them as quickly as possible.